Many vendors call this Endpoint Detection and Response (EDR) or Extended Detection and Response (XDR). Microsoft calls it Defender for Business. Most people have yet to realize that Defender for Business includes automated investigation and response. When a malware incident is detected, Defender will take action to shut down the malware and prevent the spread. An investigation will automatically be opened and any further alerts will be associated with the case.
Pre-requisites
- Have your devices gathered into groups
- If you want to have different levels of automated remediation and investigation then setup groups for that purpose. One reason you might want to have different group is privacy. Another might be that you need to exempt a folder from any action by Defender. For small companies, I prefer to just have one fully automated group unless there’s a compelling reason to do otherwise.
- Have the Defender sensor deployed to all devices
- Make sure that Defender Anti-Virus is not disabled or uninstalled
- Make sure that devices are running on the following supported OS’s
- Assign a license that includes Defender for Business like M365 Business Premium
Configure Defender for Business
The next thing we have to do is configure Defender for Business for Automated investigation and response.
Navigate to https://security.microsoft.com and then click on Settings. It is near the bottom of the menu. Now navigate through Settings>Endpoints>Permissions to Device Groups. Click the + sign to add a device group.
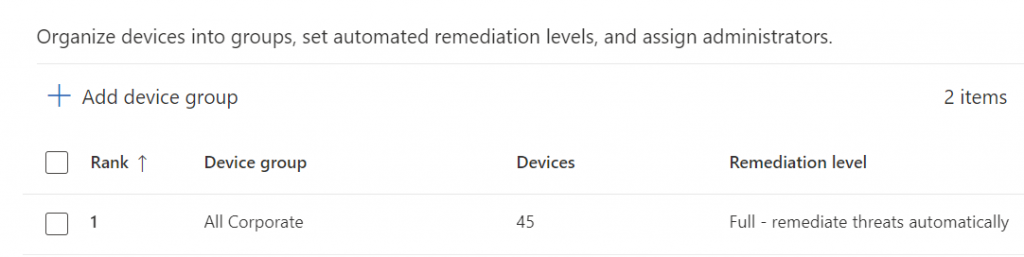
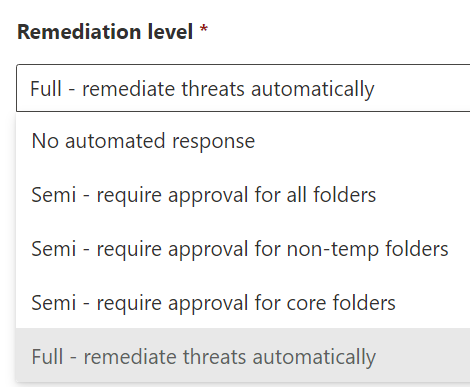
Configure the device group for full automatic remediation. When you’ve completed that, create other device groups for limited or no remediation as required for your environment.
Reviewing and Managing malware cases
Still in https://security.microsoft.com Visit the Action Center to find out what Defender has been doing on your behalf.
In the Action Center you’ll find two tab – Pending and History. The Pending tab is a list of on-going investigations. The History tab is a list of completed investigations.
Clicking on either one of them results in a fly-out column on the right that goes into details and allow you to take actions upon the item.
There are many types of incidents. Fortunately, I don’t have any complex ones to show you. Just a few ordinary situations. For each incident you’ll have the same set of columns. Date, ID, description, action, details, entity type, decision, decided by, action source and status. Imagine the two figures below side-by-side as a single entry.
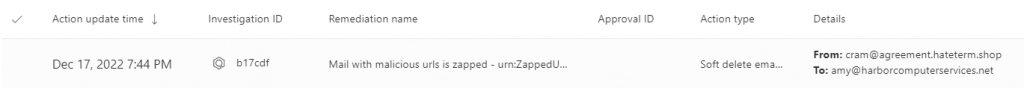
Click on the item to view the fly-out details and choose whether to take additional action upon the item. For email items like the one above there isn’t much to view. However for other types of malware there will be a little to a lot, depending on whether the malware was activated or not.
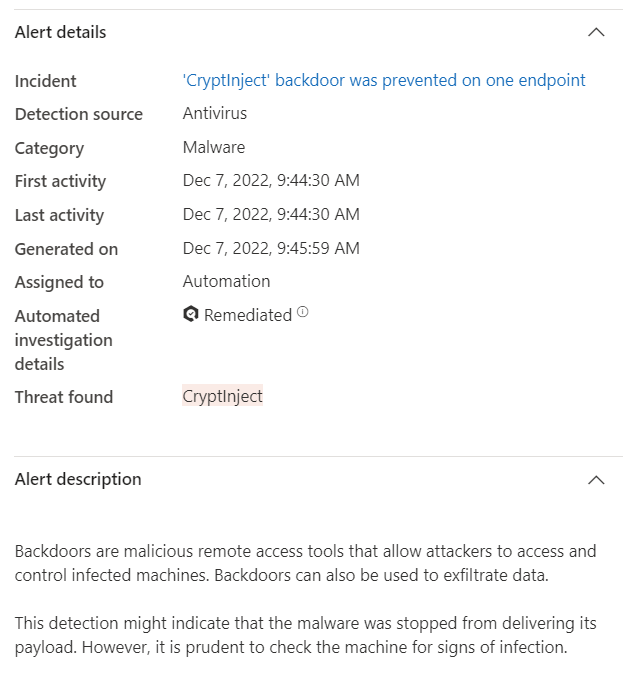
Here we see a case where a clients website backup contained malware.
The site was infected and so was the most recent backup.
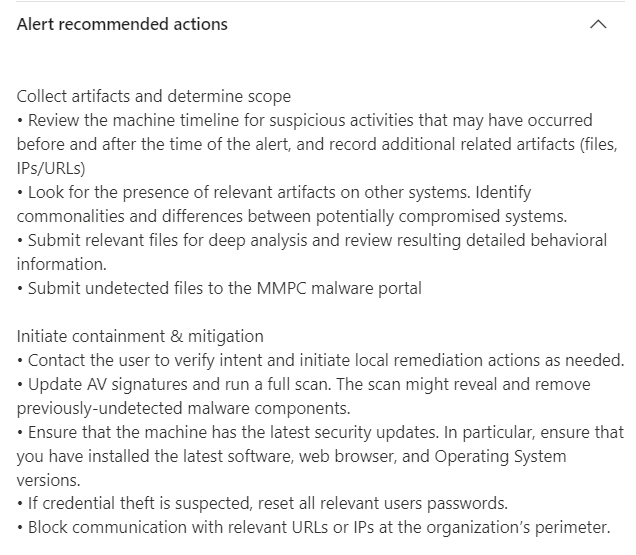
In this case, Defender quarantined the file, provided an alert and although the malware wasn’t activated, also provided information for additional action that we might want to take if we suspect additional activity around this event.
Additional information about the location, IP address, status and other details about the device where also included.
Defender for Business is a powerful tool that is included in Microsoft 365 Business Premium or available as a reasonably priced add-on for other licenses. Having an automated ERD/XDR solution is required by most cyber insurance policies and many regulatory compliances. Defender for Business is your built-in solution.
If you like this content please join our Endpoint Manager, Lighthouse & Defender group. https://www.facebook.com/groups/endpointmanager
If you’d like to read more about configuring Defender for Business, you can find more blog posts here.
All we do is support IT professionals. Microsoft 365 technical assistance, Super Secret News, Security community, MSP Legislation community, EndPoint, Defender and Lighthouse community, Peer groups, Kits, papers, Business consulting and more. https://www.thirdtier.net




