I guess because I had a section on this topic back in 2021 when I did the Don’t Miss This Setting webinar series, I felt like I had blogged about this before. Turns out I haven’t! So today, I’m going to show a couple of methods for protecting your business from OAuth permission elevation, sketchy OAuth apps, and where to set your preference for who gets to bring OAuth apps into your network. As an added bonus these settings will also help you control Shadow IT. We’ll use the Microsoft 365 tenant with at least M365 Business Premium plus Defender for Cloud licensing.
User and Admin Permissions Consent in Entra ID
Let’s start with application consent. In Entra ID, navigate to Identity, Applications, and Enterprise Applications. Then in the Security sections, select Consent and permissions. You should see something very much like the screen below.
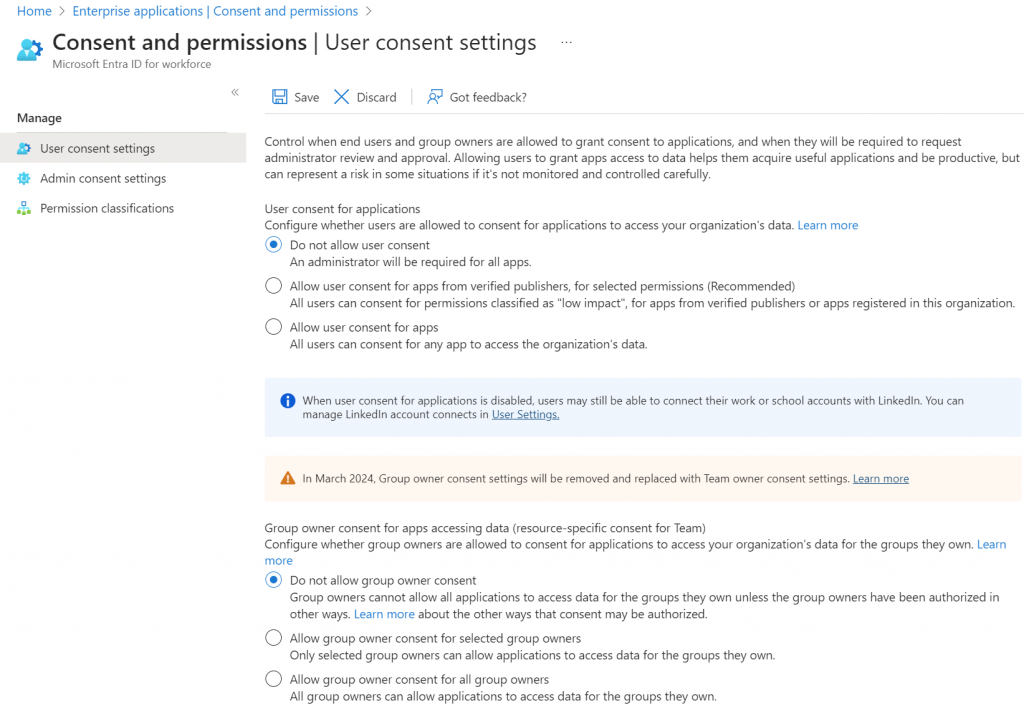
My company is small and works with small businesses, so the churn of apps isn’t high. This allows us to easily use the strictest option, that always requires admin consent to approve new app permissions. If you chose the mid-range option, which is Microsoft’s recommendation, then make sure to only allow users to approve the most basic of permissions.
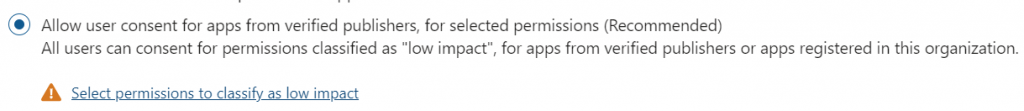
In that case, you’ll select the middle option, and then click on the Select permissions to classify as low impact link.
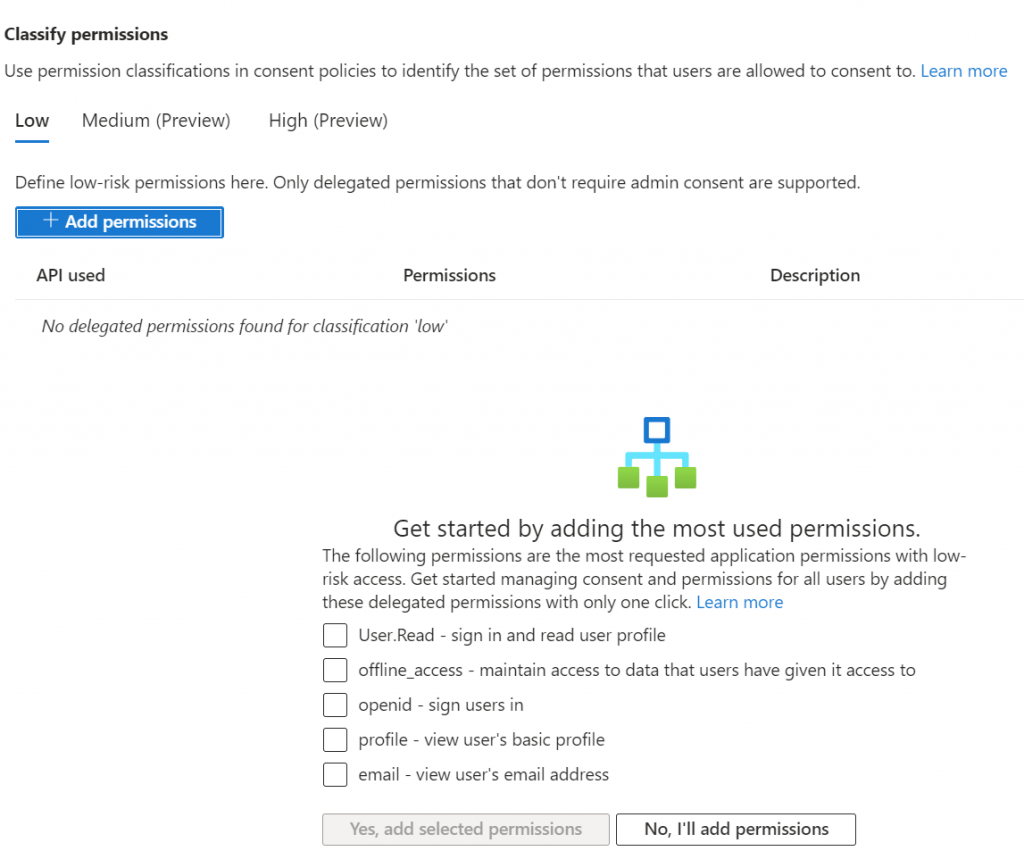
Select as few permissions as possible to reach your goal. Read only permissions and those with only access to already public information like profiles and email addresses make sense here. Microsoft has suggestions for you choose from, as shown below.
Save your changes.
You will also notice similar and separate settings for Microsoft Teams on this page. Follow the same procedure to set those.
Move down to the admin consent menu item. This is where you will send the admin notification from users that they require assistance to set permissions for a new app.
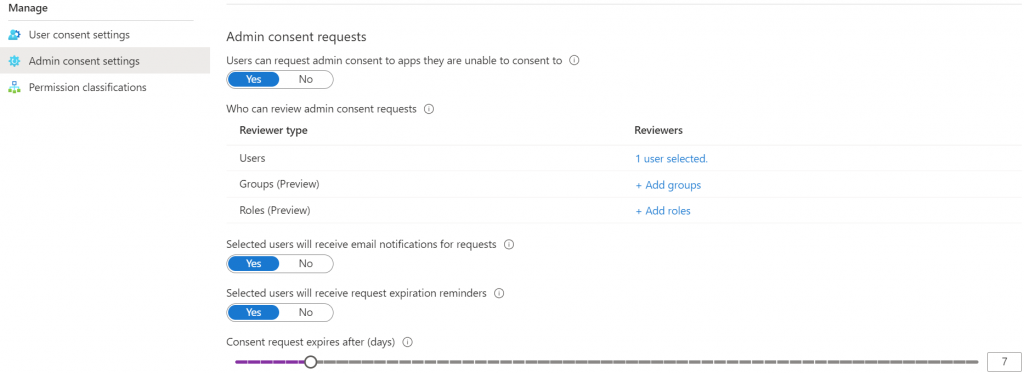
When an app asks for permissions that the user is unable to grant, there will be a button for them ask for admin consent. In this screen, as shown above you need choose the user, group or role that will be notified. The admin will be notified by email. If you want that to go to your helpdesk then you’ll want to first add your helpdesk email address as a contact, then select the group it is associated to here. In addition, you’ll need to set a number of days before the request from the user expires.
Configure OAuth policies
Now let’s create a policy in Defender for Cloud Apps to help us manage OAuth apps. Navigate to Https://security.microsoft.com and browse down through the menu then expand the Cloud apps section. Finally expand policies and choose Policy Templates. You should see a screen like the one below and be in the Policy Templates section.
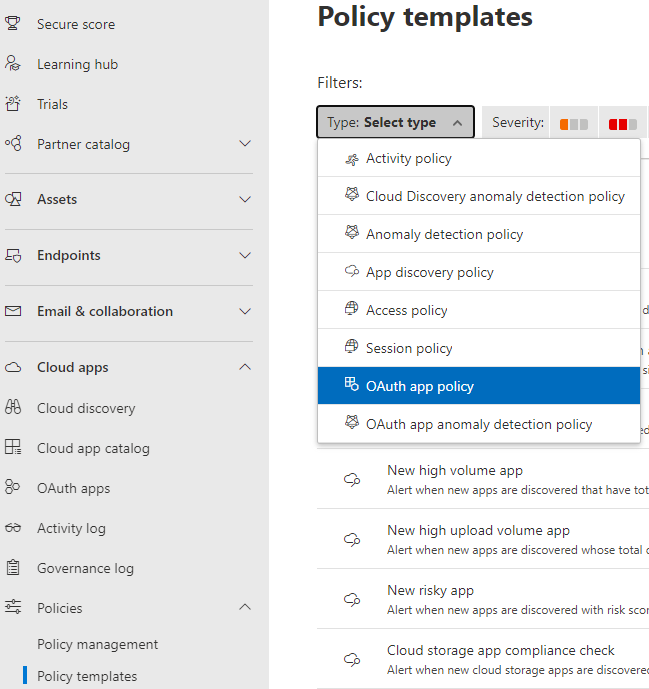
I always have trouble with the filtering function here. So instead, we are going to search for the templates that are available to help us managed OAuth. Select All Policies and then in the Name field type misleading as shown in the figure below.
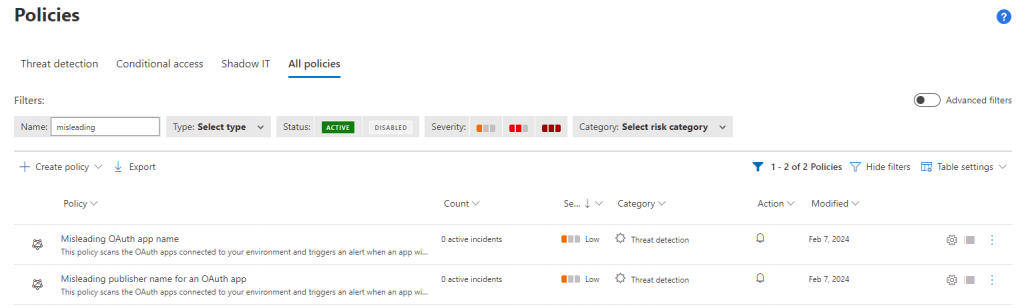
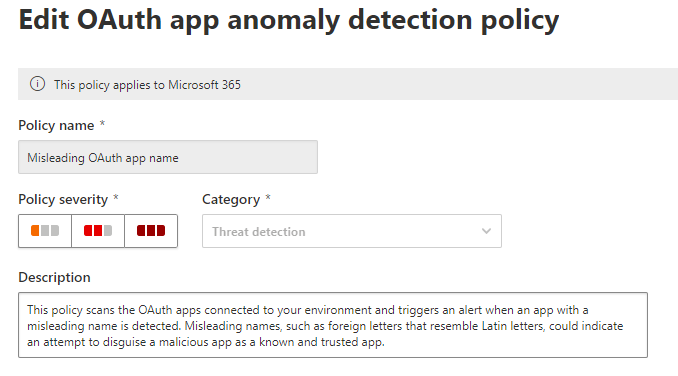
Select the policy Misleading OAuth app name. This policy will generate an alert when an oddly named OAuth app appears on your network. Decide where you want the alert to be delivered.
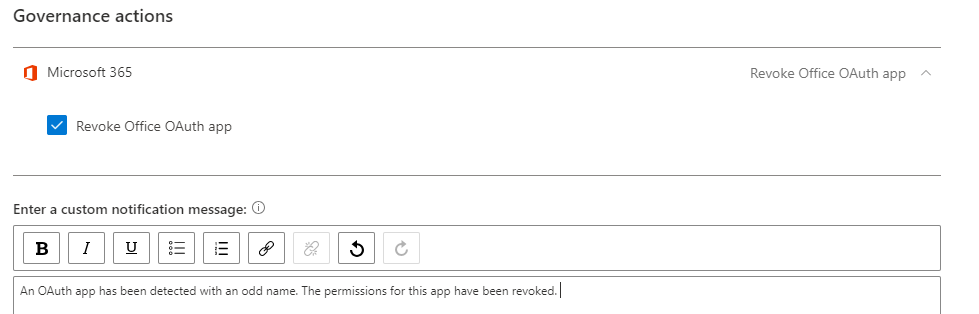
Next, expand the Governance area and check the box for Revoke Office OAuth app. What will happen now, is that if an app triggers this policy, the apps permissions will be revoked, and an alert will be delivered to the admin. Be sure to write a short description, so the admin knows what this alert means. Hopefully they won’t see this alert often and so they will need the memory prompt.
Follow the same procedure for the following policies:
- Misleading OAuth app Consent
- Misleading publisher name for an OAuth app
- Suspicious OAuth app file download activities
- Unusual additional of credentials to an OAuth app
- Unusual ISP for an OAuth app
After adding these five alerts and revoke governance actions to the first three, you will have prevented misleadingly named apps, potentially malicious apps, apps with misleading publisher names, apps performing unusual amounts of file downloads, the addition of credentials to OAuth, and apps with a strange ISP for an OAuth.
Finally, clear all filters and then select Disabled in the status section. Give it a moment and any Defender for Cloud policies that are not enabled will be displaced. Verify that all of the policies you created above are enabled.
Managing existing OAuth apps
In the Defender portal, https://security.microsoft.com/, navigate down the menu to Cloud Apps. Select OAuth apps from the menu. This will bring you to the Manage OAuth apps screen shown below.
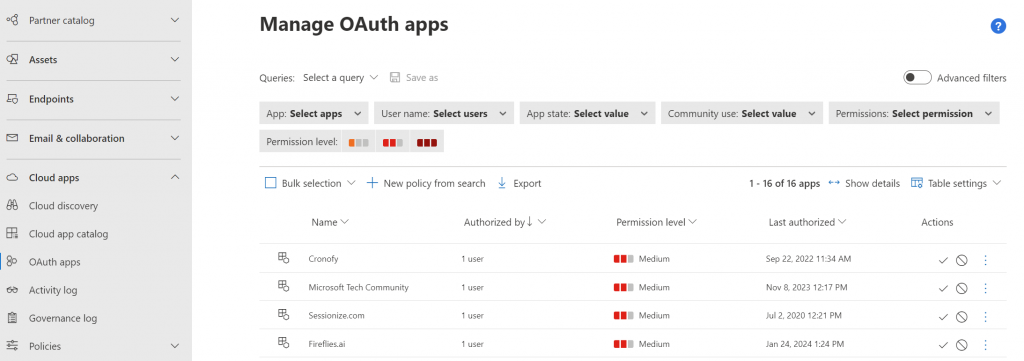
Here we have a list of OAuth apps that have been approved and are being used in our network. Clicking into an item provides the details of the permissions it has, who is using it, URL to the app, and more.
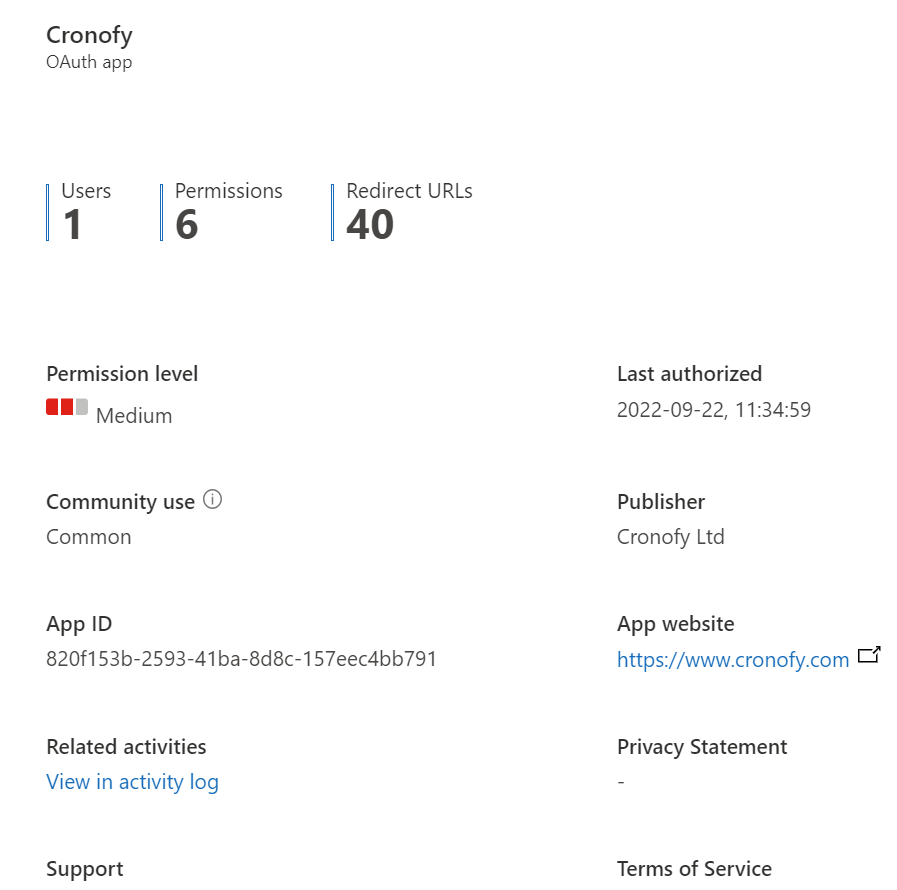
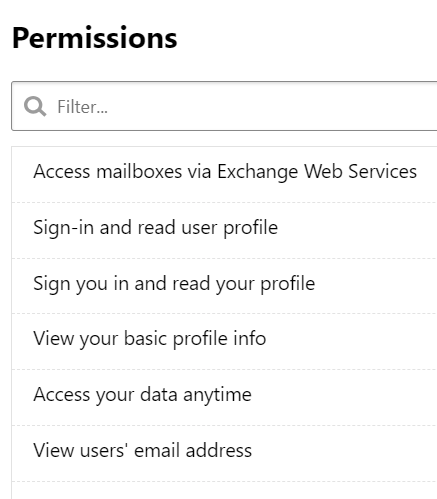
Banning an app
Once we’ve reviewed that information, we can optionally choose to approve or block the app. When you ban an app, you’ll be offered an opportunity to send the user that approved the app a message. Below you see the default message that Microsoft provides. You do have the ability to customize the message.
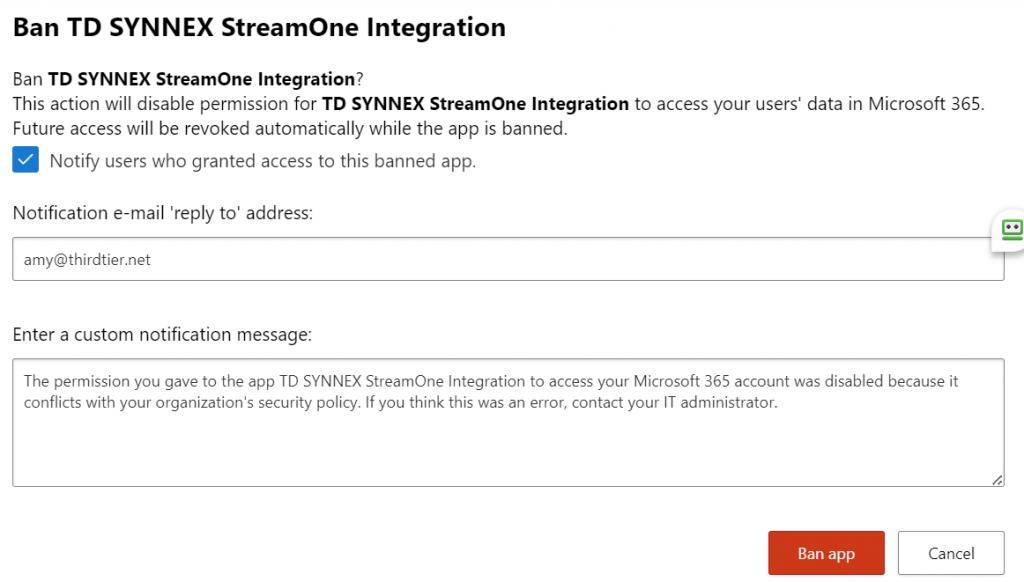
You should expressly approve of any authorized apps. Going through and doing this for each OAuth app previously approved in your organization can be time consuming and painstaking. But once you’re done, you’re done. From this point you’ll just manage any new app request as it comes in.
Configuring your Microsoft 365 tenant using Entra and Defender for Cloud apps will help protect you against the growing threat from OAuth apps.
More learning:
Manage OAuth Apps https://learn.microsoft.com/en-us/defender-cloud-apps/manage-app-permissions?source=recommendations&WT.mc_id=%3Fwt.mc_id%3DM365-MVP-33230
Investigate Risky OAuth apps https://learn.microsoft.com/en-us/defender-cloud-apps/investigate-risky-oauth?source=recommendations&WT.mc_id=%3Fwt.mc_id%3DM365-MVP-33230
Create OAuth app anomaly detection policies https://learn.microsoft.com/en-us/defender-cloud-apps/app-permission-policy?WT.mc_id=%3Fwt.mc_id%3DM365-MVP-33230
All we do is support IT professionals. Security community, MSP Legislation community, EndPoint, Defender and Lighthouse community, Peer groups, courses, papers, Business consulting and more. https://www.thirdtier.net





3 thoughts on “How to secure your network from OAuth permissions”
Interesting but with the 365 free level of Defender I don’t see the option for Cloud Apps, in fact most of the advanced features of the Microsoft 365 suite seem to be hidden behind the E5 paywall.
It’s not an e5 paywall. It’s available in many forms. The one I recommend is business premium. Entra free is only for use with companies that already have significant on-premises security infrastructure playing the role for them. You have to invest in security somewhere