The other day I went down a rabbit hole while attempting to help someone and I ended up learning about destructive (the default) and non-destructive PIN reset for Windows. I ended up deploying non-destructive PIN reset into our tenant and you might want to too. Microsoft has an excellent article on how to do this but of course the reality is a bit different. What follows is my experience and tips
Why deploy non-destructive PIN reset?
“During a destructive PIN reset, the user’s existing PIN and underlying credentials, including any keys or certificates added to their Windows Hello container, will be deleted from the client and a new logon key and PIN are provisioned.”
If you’ve reset your PIN on your device and then had to go through a bunch of accept this, accept that, for a while afterwards, this is why. Avoiding that situation seems like enough reason to go through this exercise.
“When non-destructive PIN reset is enabled on a client, a 256-bit AES key is generated locally and added to a user’s Windows Hello for Business container and keys as the PIN reset protector. This PIN reset protector is encrypted using a public key retrieved from the Microsoft PIN reset service and then stored on the client for later use during PIN reset. After a user initiates a PIN reset, completes authentication to Azure, and completes multifactor authentication, the encrypted PIN reset protector is sent to the Microsoft PIN reset service, decrypted, and returned to the client. The decrypted PIN reset protector is used to change the PIN used to authorize Windows Hello for Business keys and it is then cleared from memory.“
This still sounds safe so let’s proceed.
Using EndPoint Manger to deploy non-destructive device PIN reset
The first thing that we have to do is install the Microsoft PIN reset service into our Azure AD tenant. To do that we visit this website and logon as a global admin. And when prompted, accept the assignment of permissions. Here’s the first place where Microsoft’s article goes astray. Once you’ve gone through that process you will see that you have half of what you need in Azure AD. The first time you run it, it installed the Microsoft Pin Reset Service Production and the second time you run it, it installs the Microsoft Pin Reset Client Production. Run through the process again for it to install the second half. When successful you’ll have two new Enterprise Apps installed.
Verify that both are there by navigating to Azure AD, Enterprise Applications and searching for Microsoft.

Create a Configuration profile to enable Identity Protection PIN reset. Here again the article goes astray. It sends you on a wild goose chase looking for Endpoint Security > Account Protection > Properties which doesn’t exist. Instead what we’re going to do is create a new Configuration Profile.
Create a new configuration profile. Select Windows 10 and newer for the platform. Select Identity Management for the profile. Here only need to set Configure Windows Hello for Business to Enable and Enable PIN recovery to Enable. Assign this profile to All Users or some subset of users of your choosing.
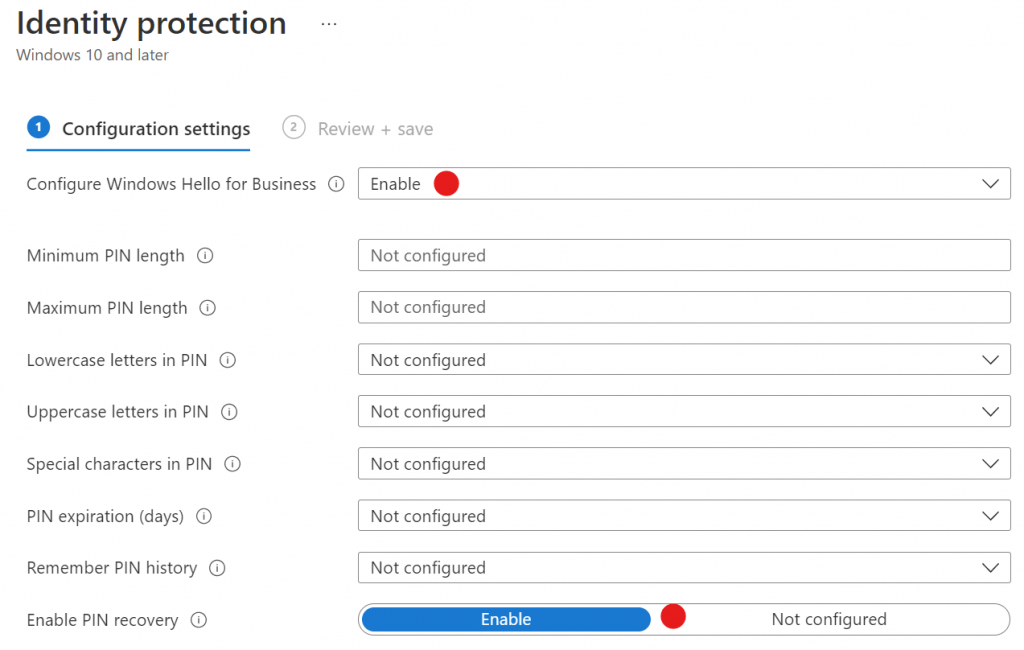
Make sure the policy is effective
For this configuration to take effect the target computer has to reboot. To test mind, I forced a sync by going to Devices, selecting my device and choosing Sync. The reboot was still required. Once rebooted run this command, dsregcmd /status to check if the device is now able to perform a non-destructive PIN reset.
When the policy is in place you’ll have the following
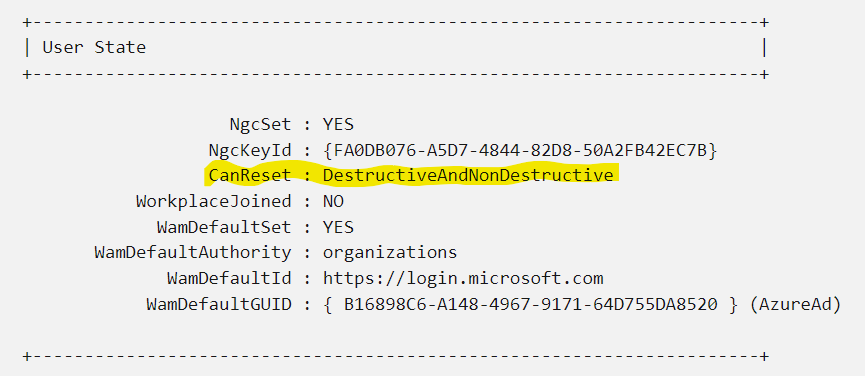
Now when the computer user chooses to reset their PIN, only the PIN will be reset and your certificates and such won’t be lost. The user will still need to know their password and/or account recovery information. So this does not let you off the hook for providing a password management tool that can be accessed from their phone. No one remembers their computer password because you never need the thing anymore.
If you like this content please join our Endpoint Manager, Lighthouse & Defender group. https://www.facebook.com/groups/endpointmanager
All we do is support IT professionals. Microsoft 365 technical assistance, Super Secret News, Security community, MSP Legislation community, EndPoint, Defender and Lighthouse community, Peer groups, Kits, papers, Business consulting and more. https://www.thirdtier.net




