According to Microsoft, PlugX malware uses ACSII extended character encoding to hide code. This code can then be autoplayed upon insertion. To void this malware, we need to make sure that AutoRun is off for removable media and that we block untrusted and unsigned processes from running via USB.
Turn off AutoRun
To turn off AutoRun we’ll create a configuration profile using Intune endpoint manager.
Create a new configuration profile using the Settings picker. Seach for AutoPlay and then select the item, Administrative Templates/Windows/Components/AutoPlay Policies, as shown in the figure below.
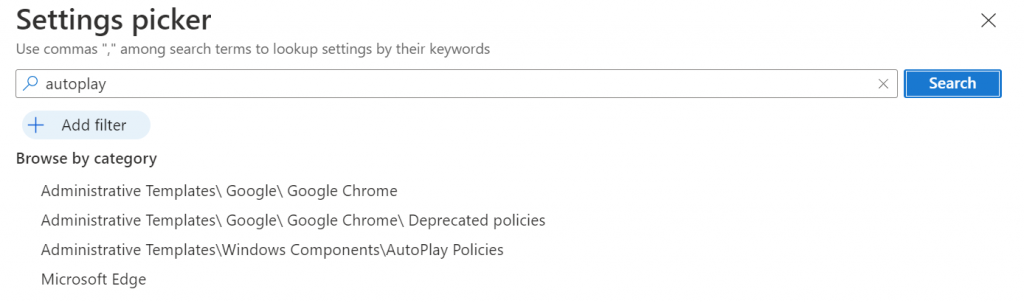
Next, we’re going to turn on all of the blocks for removable media. Select the items shown in the figure below.
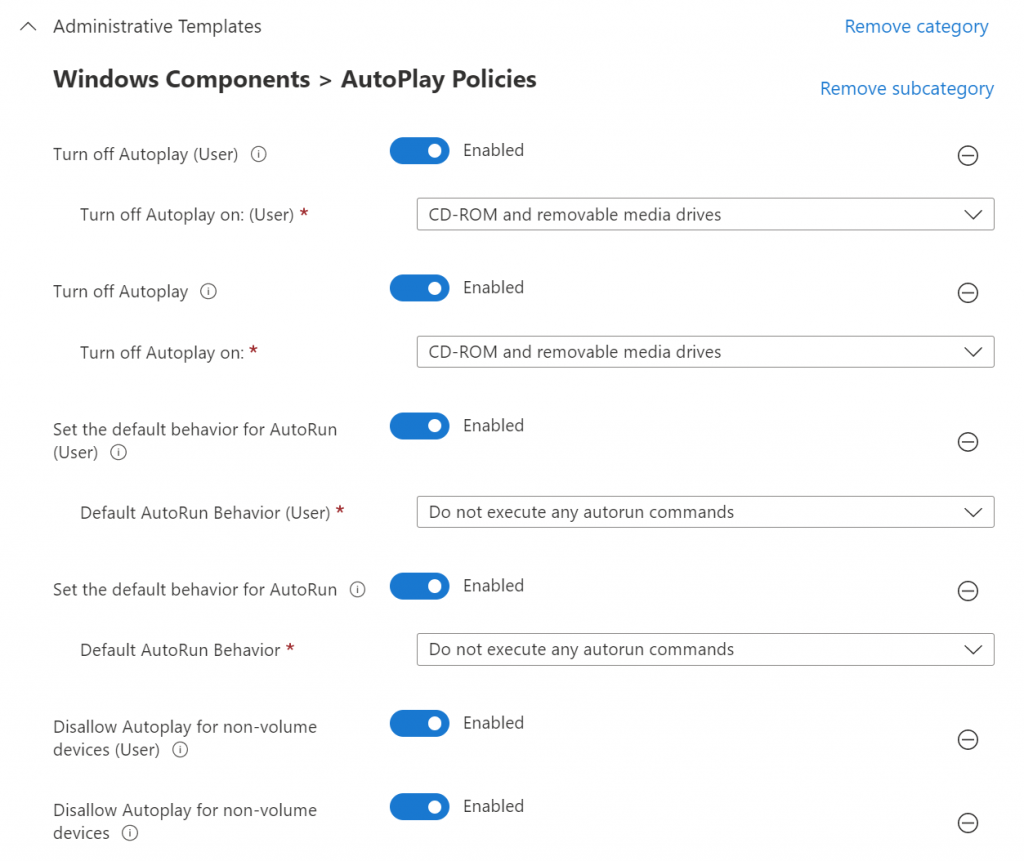
Finally, apply this policy to the All Devices group because we’d like this policy to run whether anyone is logged into the computer or not.
Block untrusted and unsigned processes from running via USB
To block untrusted and unsigned processes from running via USB, we will turn on an Account Surface Reduction rule.
In Intune, navigate to Endpoint Security, then Attack Surface Reduction. Edit or create your rule with the following item set to Block.
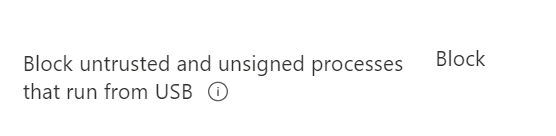
Once these two items have been set the ability of PlugX to take advantage of innocent people should be thwarted.
If you’d like to read more about configuring Intune endpoint manager, you can find more blog posts here.
All we do is support IT professionals. Microsoft 365 technical assistance, occasional Newsletter, Security community, MSP Legislation community, Intune, Defender and Lighthouse community, Peer groups, Papers, Business consulting and more. https://www.thirdtier.net and https://www.facebook.com/thirdtier for the community groups listed above.




