It’s a common uncommon occasion when a person gets a new device that isn’t yet registered with Azure for MFA and its the device that was their authenticator. They find that they are unable to register the new device because they haven’t yet registered for MFA and they can’t register for MFA because they haven’t yet registered the device and MFA registration is set to only occur from a registered device. Having MFA only be allowed from a registered device is an excellent way to reduce your threat footprint but it can result in this dilemma.
There are a few ways to resolve this problem.
- Add the individual as an exception to the MFA conditional access policy that requires them to use a registered device to establish MFA from.
Since these are always one-off problems, this is not a bad solution. The problem gets resolved. However, since we know that most admins are lazy there’s a large opportunity for the admin to not remember to circle back and remove that user from that exception once MFA registration has been completed. In an online conversation on this topic, it was felt that the lazy admin was too big of a risk to not address.
2. You can create an exclusion group and have the group in the exclusion part of the policy. Then when you add someone to the group. The problem gets resolved. However, since we know that most admins are lazy there’s a large opportunity for the admin to not remember to circle back and remove that user from that exception group once MFA registration has been completed. In an online conversation on this topic, it was felt that the lazy admin was too big of a risk to not address.
I could repeat the text above under solution #1 or just say ditto. Lazy admin is too big of a risk not to address.
3. You can create an exclusion group and run a script each night to remove any users from that group.
This excellent solution was offered by another. It’s a good way to resolve the lazy admin problem. However, it does require a machine be left on to run the script each night or that you give access to another automation tool that will run the script. And I think that this is only going to apply successfully if you have an on-premises AD.
4. You can create an exclusion group and use powershell to add the user to that group including an expiration on the group membership. Add-ADGroupMember -Identity ‘Name of the exclusion group’ -Members ‘friendly name of user’ -MemberTimeToLive (New-TimeSpan -Days 2
The MemberTimeToLive parameter offers these features. in our same, New-TimeSpan -Days 2, could that also be New-Timespan -Hours 2? Perhaps it could.
-MemberTimeToLive
Specifies a Time to Live (TTL) for the new group members.
| Type: | TimeSpan |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
However, this carries the same problem in that it only works on AD, not Azure AD.
5. Fortunately Microsoft has come up with the solution for Azure AD! It’s the Temporary Access Pass. In this scenario, a temporary access pass policy is created as an authentication method. Now when you need to give an individual access to their account to complete the MFA registration process, you go in and create a temporary access pass in their account and give them the code that it generates. These passes can be from 1-8 hours long. Notable, in the article is mentions that they have only 10 minutes to complete the MFA registration process once they’ve begun it.
Here’s what the options look like. By default the maximum length of time is 8 hours.
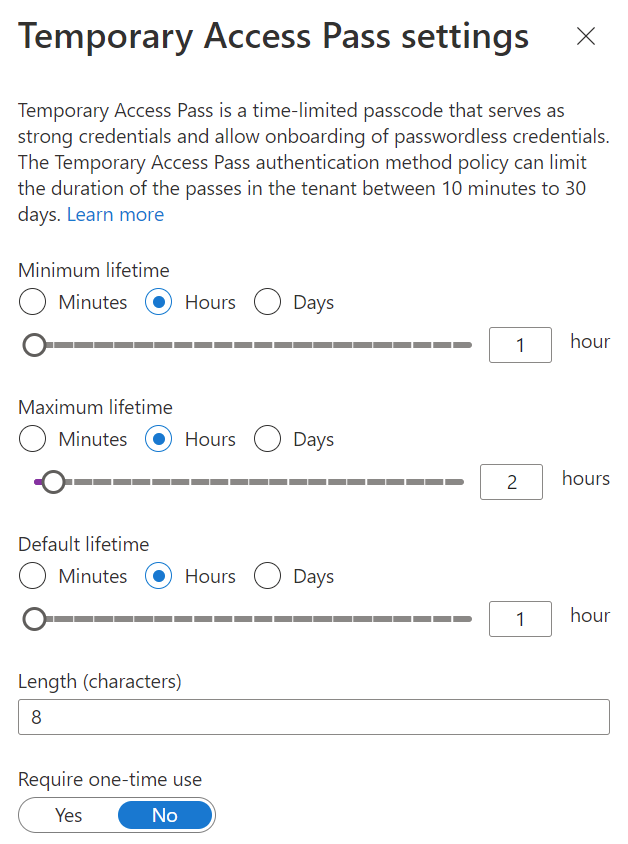
Procedurally what the admin will do after the policy has been enabled on the tenant is to go the user account, generate a temporary access pass, setting the length of time that it will be good for, for that individual. Provide that individual with the code that is generated. At this point, assuming that you are requiring MFA registration when they successfully login they will be prompted to complete that process. All of the details are in the URL above. It does not appear complex at all and a trusted friend has tested it and it works!
As everyone should be moving along toward using Azure AD this last solution is going to be the best one. Bravo Microsoft for making it simple.
All we do is support IT professionals. Microsoft 365 technical assistance, Super Secret News, Security community, MSP Legislation community, EndPoint, Defender and Lighthouse community, Peer groups, Kits, papers, Business consulting and more. https://www.thirdtier.net




