A couple of situations have given rise to the need to prevent the downloading of data to untrusted devices. Given that organized criminals are now playing the long game, sitting in your network for long periods of time just looking around and gathering data, and given that businesses have employees working from untrusted shared computers at home, we decided that there was a significant need to prevent the downloading of files onto machines that were not under management.
Unfortunately, this solution requires Microsoft 365 E5 licensing to achieve but if you’re looking for another reason to justify the upgrade, then add this to the list.
Endpoint Management
Endpoint management isn’t just a Microsoft product. It’s also a concept and that concept includes a group of features and products. Blocking downloads falls into Conditional Access’s area of responsibility using session monitoring.
Build the Conditional Access policy
Let’s build a conditional access policy that prevents anything but Azure AD Joined devices from downloading data.
Start by choosing the group of users that this policy will apply to. Here’s I’ll chosen our custom All internal users group.
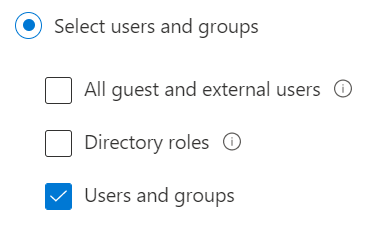
Next select the app that this policy will apply to. I’m going to choose Office 365 since we want to protect our cloud data.
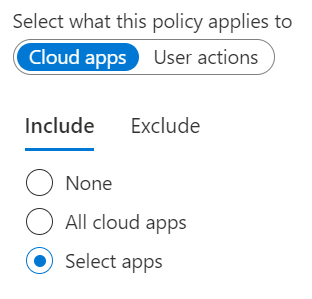
For this policy I’m using the still in preview feature, Device State. Once this comes out of preview there may be some changes.
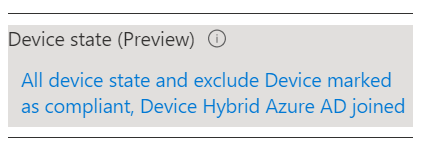
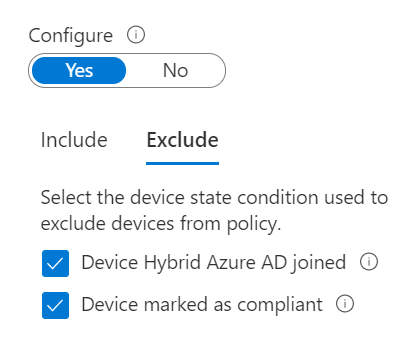
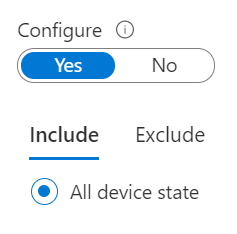
Now for the confusing part. We need to include all Device and then exclude the two available states. The two device states available to us are Hybrid Joined and Compliant. I worried a but because our trusted devices are Azure AD Joined, not Hybrid but it turns out that these selections work just fine for both.
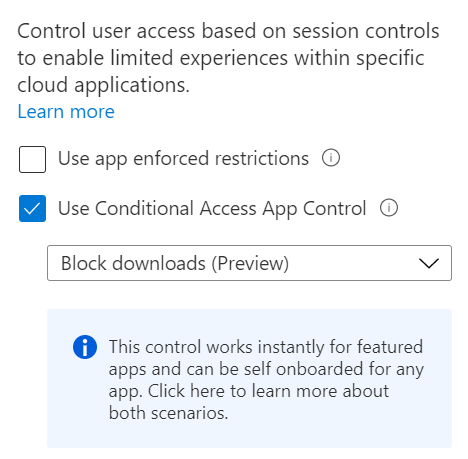
Next, we’re using another feature currently in preview in Access Controls – Session. There’s a message here about featured apps which are essentially the Office 365 apps but you can add others by following the link to learn how.
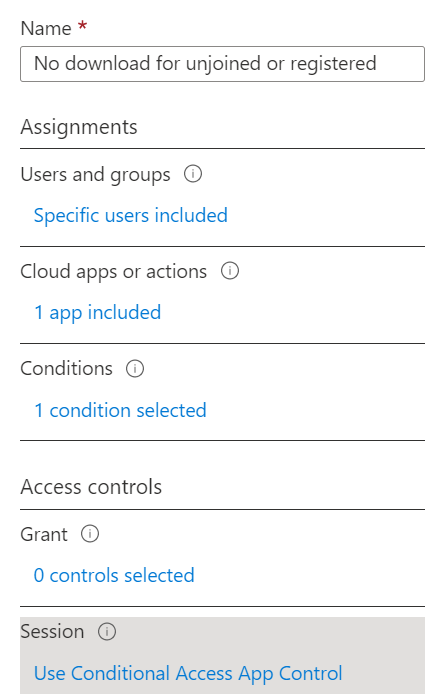
Our policy then looks like this:
Why does this work?
I think that Microsoft says it best in their documentation. “The conditions define who (user or group of users) and what (which cloud apps) and where (which locations and networks) a Conditional Access policy is applied to. After you’ve determined the conditions, you can route users to Cloud App Security where you can protect data with Conditional Access App Control by applying access and session controls.”
Which means that this policy is dependent upon Cloud App Security but in this case, they’ve brought all of the settings to us and we don’t have to configure anything in Cloud App Security, the policy selections we’ve made do that for us.
What else can we do?
There’s a lot to this new feature set. With these options your creativity is really the limit. Again from: Protect with Microsoft Cloud App Security Conditional Access App Control | Microsoft Docs
- Prevent data exfiltration: You can block the download, cut, copy, and print of sensitive documents on, for example, unmanaged devices.
- Protect on download: Instead of blocking the download of sensitive documents, you can require documents to be labeled and protected with Azure Information Protection. This action ensures the document is protected and user access is restricted in a potentially risky session.
- Prevent upload of unlabeled files: Before a sensitive file is uploaded, distributed, and used by others, it’s important to make sure that the file has the right label and protection. You can ensure that unlabeled files with sensitive content are blocked from being uploaded until the user classifies the content.
- Block potential malware: You can protect your environment from malware by blocking the upload of potentially malicious files. Any file that is uploaded or downloaded can be scanned against Microsoft threat intelligence and blocked instantaneously.
- Monitor user sessions for compliance: Risky users are monitored when they sign into apps and their actions are logged from within the session. You can investigate and analyze user behavior to understand where, and under what conditions, session policies should be applied in the future.
- Block access: You can granularly block access for specific apps and users depending on several risk factors. For example, you can block them if they are using client certificates as a form of device management.
- Block custom activities: Some apps have unique scenarios that carry risk, for example, sending messages with sensitive content in apps like Microsoft Teams or Slack. In these kinds of scenarios, you can scan messages for sensitive content and block them in real time.
If you’re thinking that all of this looks familiar well it does. This is the work of reverse proxy and those that have followed me and Microsoft along the path from ISA are going find themselves in familiar territory, at least from a conceptual point of view.
If you like this content please join our Endpoint Manager, Lighthouse & Defender group. https://www.facebook.com/groups/endpointmanager
All we do is support IT professionals. Help for IT Pros, Super Secret News, Security community, MSP Legislation community, Kits, papers, MSP training and more. https://www.thirdtier.net




