Microsoft’s Business Premium licensing is a real gift to the SMB market. It’s a full EDR solution. But let’s say that you’ve come across a situation, and you want to remove a device from the network – remotely, while you investigate. Interestingly this device, need not be enrolled in Defender for Business. It can be an unmanaged device too.
While you don’t get to choose between Isolate and Contain it is important to know why you are being presented with a particular option and how each experience behaves.
Contain a device
Using Microsoft Defender for Business, which is built into Microsoft 365 Business Premium, launch https://security.microsoft.com, navigate down to Assets and click on devices. Check the box to select the machine that you want to isolate.
At the top of the page, select the ellipse and choose Contain device.
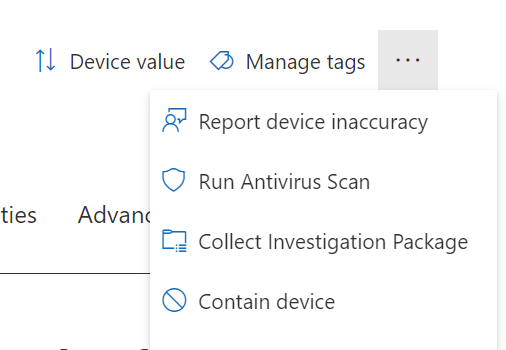
The Contain device action will prevent other managed Windows devices from communicating with this device. Defender identifies the device and should the device change IP addresses, the update will be sent out and adjustments made so that it remains contained.
From Microsoft’s article on the containment action,
- If a contained device changes its IP address, then all Microsoft Defender for Endpoint onboarded devices will recognize this and start blocking communications with the new IP address. The original IP address will no longer be blocked (It may take up to 5 mins to see these changes).
- In cases where the contained device’s IP is used by another device on the network, there will be a warning while containing the device, with a link to advanced hunting (with a pre-populated query). This will provide visibility to the other devices using the same IP to help you make a conscious decision if you’d like to continue with containing the device.
- In cases where the contained device is a network device, a warning will appear with a message that this may cause network connectivity issues (for example, containing a router that is acting as a default gateway). At this point, you’ll be able to choose whether to contain the device or not.
After you contain a device, if the behavior isn’t as expected, verify the Base Filtering Engine (BFE) service is enabled on the Defender for Endpoint onboarded devices.
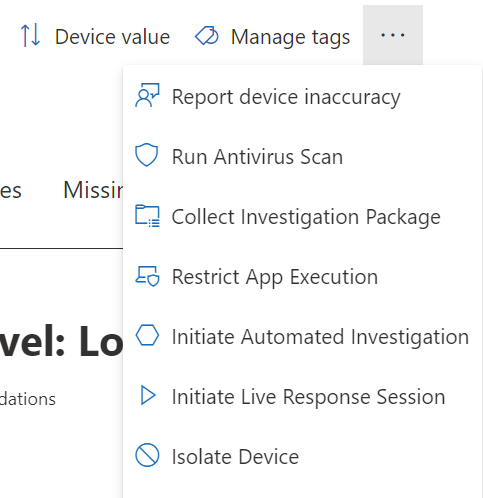
Isolate a managed device
Managed devices are defined as those that have the Endpoint sensor installed. When that is the case, you will notice that the available action is now called Isolate device.
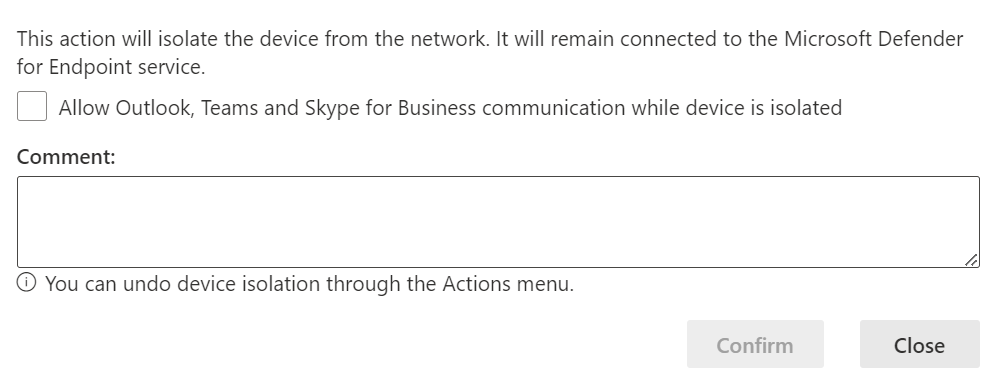
The Endpoint sensor, leverages control over the local device networking services to provide you with option as seen in the figure below. Enter a comment and choose whether you want to continue to allow Teams, Outlook and Skype to function. All other network communications will be blocked. Click Confirm.
Nearly instantly the user will see a toast message that the network has dropped and they’ll instantly notice too that they cannot get to the internet, nor any local resources. However, you will still have access to the machine via Defender for Endpoint.
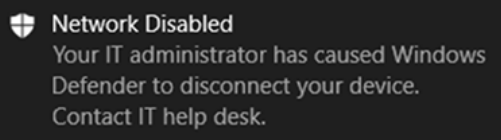
The action here is different. Because the sensor is installed, the device is prevented from communicating on the network, whereas with containment it was the other way around.
From Microsoft’s article on the Isolate action:
- Isolating devices from the network is not currently supported for devices running macOS. For macOS, use live response to run the action. For more information on live response, see Investigate entities on devices using live response.
- Full isolation is available for devices running Windows 11, Windows 10, version 1703 or later, Windows Server 2022, Windows Server 2019, and Windows Server 2016.
- You can use the device isolation capability in public preview on all supported Microsoft Defender for Endpoint on Linux listed in System requirements.
- Selective isolation is available for devices running Windows 10, version 1709 or later, and Windows 11.
- When isolating a device, only certain processes and destinations are allowed. Therefore, devices that are behind a full VPN tunnel won’t be able to reach the Microsoft Defender for Endpoint cloud service after the device is isolated. We recommend using a split-tunneling VPN for Microsoft Defender for Endpoint and Microsoft Defender Antivirus cloud-based protection-related traffic.
- The feature supports VPN connection.
- You must have at least one the following role permissions: ‘Active remediation actions’. For more information, see Create and manage roles.
- You must have access to the device based on the device group settings. For more information, see Create and manage device groups.
- Exclusion for Linux isolation is not supported.
Return a device to the generation population
When you’re ready to release the device from either containment or isolation just go to the same ellipse as before and you’ll now find the Release action.
I recommend experimenting with these actions so that you’ve seen the behavior in person before you need it in an emergency.
If you’d like to read more about configuring Defender we’ve consolidated them for you here
All we do is support IT professionals. Microsoft 365 technical assistance, occasional Newsletter, Security community, MSP Legislation community, Intune, Defender and Lighthouse community, Peer groups, Papers, Business consulting and more. https://www.thirdtier.net and https://www.facebook.com/thirdtier for the community groups listed above.




