We run into a lot of ACL corruption issues and access issues when a folder has not been disinherited properly.
The following is the best method for disinheriting permissions a folder receives from its parent:
- Right click on the folder and click Properties
- Click the Advanced button
- Click the Change Permissions button if required
- Click the Disable inheritance button
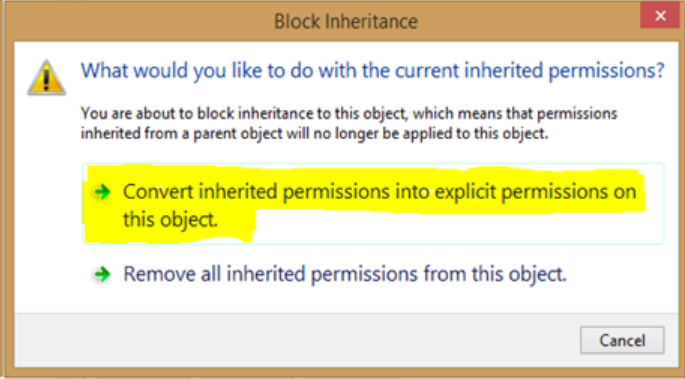
- Click the Convert inherited permissions into explicit permissions on this object.
- Click on DOMAIN\Domain Users or MACHINE\Users and then the Remove button
- This removes access to that folder to all domain users
- Add the necessary security groups and give them MOD
- OPTION: On existing folder sets one can click Replace all child object permission entries with inheritable permission entries from this object
- Does one want to click this? If there are customized permissions _below_ the folder being disinherited those permissions would be lost.
- Click Apply and OK.
From there our folder would now have the necessary permissions for users in the specific security group(s) to make changes.
We enable Access-based Enumeration on _all_ shares we deploy by default. This means that users that are not in the above assigned security group(s) will not see the folder in their File Explorer.
One of the warning signs that the above process was not followed will be for domain admin or local admin accounts to get a UAC prompt when navigating the physical folder set.
As a rule we follow a trunk –> branch –> leaf structure for our folders. All users have a single point of entry with some subfolders having their inheritance blocked.
From there we prefer to _not_ disinherit any further down-level folders unless absolutely necessary because that inevitably leads to access issues and/or permissions corruption.
Originally posted in 2015 this popular post was migrated over from our previous blog
Make your IT business better than the competition. Help for IT Pros, TechYourBooks, Super Secret News, Women in IT Scholarship program, Ransomware Prevention Kit, 365 Security kit and more. https://www.thirdtier.net