Stealing weak MFA session tokens is a technique used by criminals who successfully phish an end-user. They can then use that token to supply the MFA code when logging in as that user. Microsoft recently published an analysis of the techniques used by one popular phishing-as-a-service provider.
We’ll take that analysis and implement a solution based upon it. The two key elements of protection that we can act upon, according to the analysis are:
- Enable conditional access policies. Conditional access policies are evaluated and enforced every time an attacker attempts to use a stolen session cookie. Organizations can protect themselves from attacks that leverage stolen credentials by enabling policies such as compliant devices or trusted IP address requirements.
- Make sure continuous access evaluation is enabled in your tenant.
CA013: Require compliant or hybrid Azure AD joined device or MultiFactor for all users
Make use of the Azure Active Directory conditional access policy, CA013. This policy requires the user to have a compliant or known machine to active directory or user multifactor authentication. We will start with this template but remove the multifactor authentication option. The end result will be two policies. One that requires multi-factor authentication and one that requires a compliant or joined device.
I’m going to assume that you already have a requirement for multi-factor authentication. We will leave that policy in place.
In conditional access, choose add policy from template and choose CA103. Remove the words, “or MultiFactor” from the name of the policy. Then move to the Grant section. In this section uncheck Require multifactor authentication. And then at the bottom on the page press the Select button to save the change.
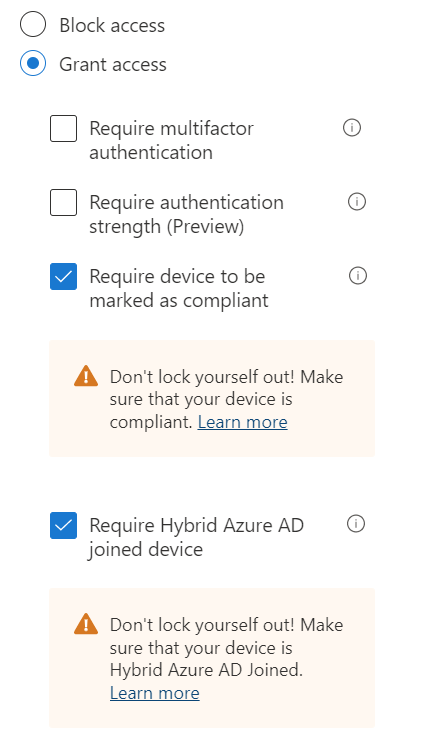
Exclude any service or emergency access accounts from the policy and then choose On or Report Only as appropriate for your environment.
Enable Continuous access evaluation
If you’re tenant has been around for a while, then you will need to follow this article to enable Continuous access evaluation. Continuous access evaluation in Azure AD – Microsoft Entra | Microsoft Learn If your tenant is new, then it will be enabled by default.
Enable a User Risk policy
Under Microsoft’s own recommendation, it says to enable a User risk policy. If you are using Microsoft 365 Business Premium, then these policies will be enabled for you by default, and you don’t have the ability to edit them. To edit these policies, you would need Azure AD P2 licensing.
In Azure AD, click into Security then Identity Protection. Click on User Risk and Sign-in Risk to view the policies. Since we don’t have the ability to edit these policies, we will ignore the suggestion to migrate this policy to conditional access. That is also not an option for M365 Business Premium users.
In the figure below the left is the default user risk policy and the right is the default Sign-in risk policy.


Implement phishing resistant MFA
Many different types of MFA are offered in Azure AD. Some of them are considered phishing resistant. These include: Authenticator app using the new experience and hardware token. What you really want to avoid is enabling SMS or eMail as a method. Phone call is also suspect in my book.
For more information and instruction on migrating to the new MFA options please see the post, Migrate to the new MFA authentication policies.
A little bit more secure every day is the security minded administrator’s task.
Read more about Azure AD in our blog.
All we do is support IT professionals. Microsoft 365 technical assistance, Newsletter, Security community, MSP Legislation community, Intune, Defender and Lighthouse community, Peer groups, Kits, papers, Business consulting and more. https://www.thirdtier.net




